Welcome to the Trezor® Login Portal — your starting point for secure access to hardware-wallet protected accounts. This guide explains the principles behind a secure connection, practical login best practices, and the checks you should perform every time you connect your device. It is intended for informational purposes and does not replace official firmware instructions, but it reflects current industry recommendations for keeping your crypto assets safe.
Understanding the secure connection
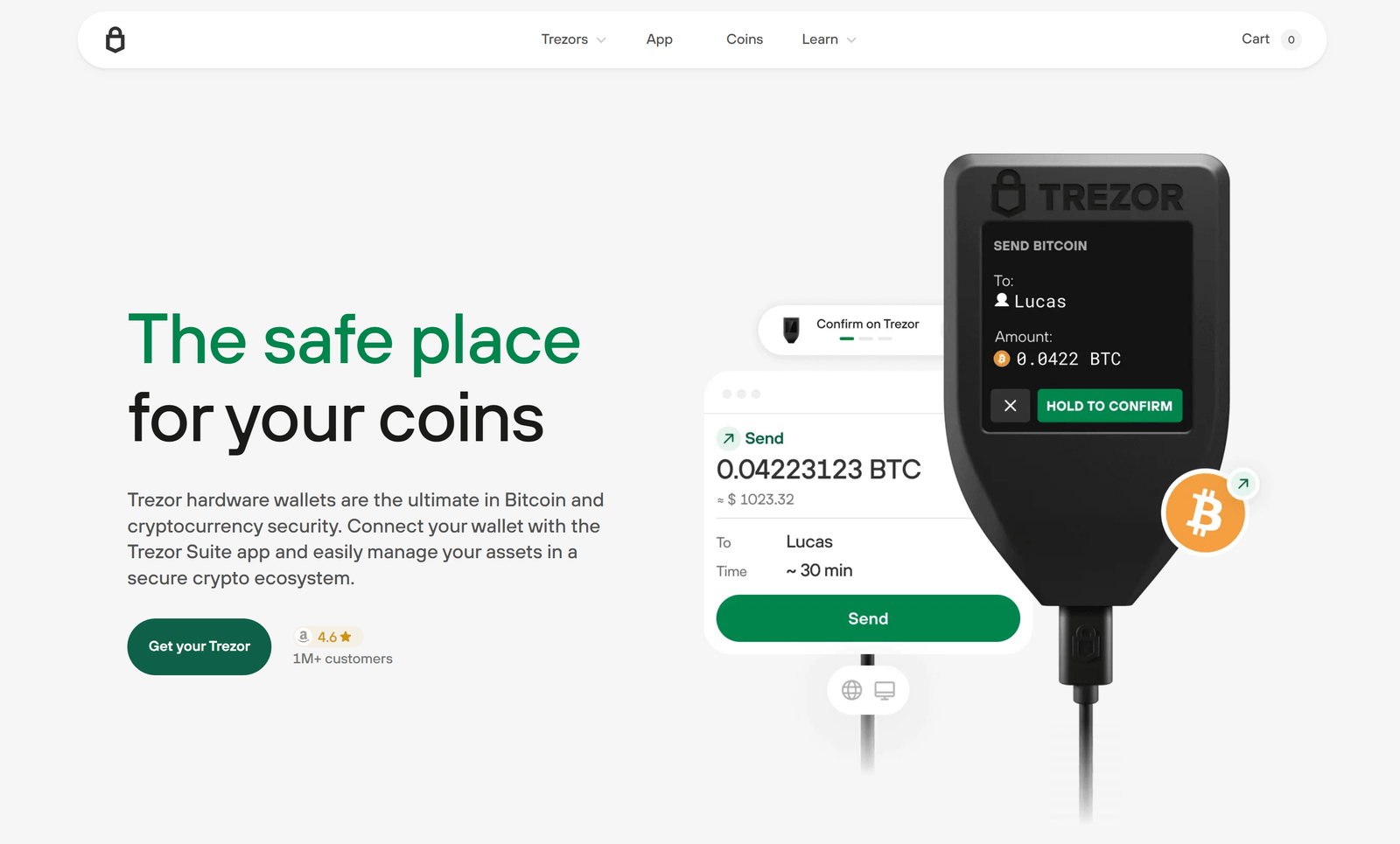
A Trezor hardware wallet authenticates transactions and stores private keys offline. The login process relies on a secure USB or WebUSB connection between your device and a trusted host (desktop or laptop). During a login session, the wallet performs cryptographic operations on-device so that private keys never leave the hardware. Confirmations, PIN entry and transaction signing are carried out locally, while the connected host handles transaction construction and network broadcast.
Preparation before connecting
Always prepare your environment before connecting. Use a fully updated operating system and browser, and apply the latest firmware updates for your Trezor device. Verify that you are visiting an authentic companion interface (official Trezor web or native application). Avoid public or untrusted networks when logging in, and prefer a private, wired network if possible. Disable unnecessary browser extensions and close unrelated tabs to reduce the attack surface.
Visual and cryptographic verification
Trust but verify. Check the host interface URL for a secure HTTPS connection and a valid certificate before proceeding. When prompted, compare device-generated fingerprints, addresses, and transaction details shown on the hardware display with those in the host application. Trezor devices display critical data on-device precisely to prevent man-in-the-middle attacks. Only approve operations after confirming that every displayed element matches your expectation.
PIN, passphrase and recovery considerations
Your PIN and optional passphrase form the core of access control. Choose a PIN that is not easily guessable, and never store it digitally in plain text. If you enable the passphrase feature, treat it as an extension of your seed — it should be secret, memorized, and stored offline if written down. Keep your recovery seed physically secure and never enter it into a computer, phone, or online form. A recovery seed is a last-resort mechanism for device recovery and must remain confidential.
Best practices for session hygiene
After completing a session, safely disconnect the device and power-cycle your host if you suspect any suspicious behavior. Regularly inspect your device for firmware authenticity by checking firmware version metadata against official release notes. Maintain minimal software on your primary crypto access machine; consider using an air-gapped or dedicated device for high-value operations. Use reputable antivirus tools and keep backups of important system files in encrypted storage.
Recognizing phishing and social engineering
Phishing is a primary vector for credential compromise. Be skeptical of unsolicited emails, messages, or social media communications urging immediate login or recovery. Official teams will never ask for your PIN, passphrase, or recovery seed. Verify any support channels through official websites and cross-check contact details. If in doubt, consult official knowledge base articles before revealing any sensitive information.
Troubleshooting common connection issues
If your device is not recognized, try a different USB port or cable; prefer original or high-quality cables. Reboot your host and re-open the official companion interface. Ensure browser permissions for USB/WebUSB are enabled and that no VPN or proxy is interfering with local device enumeration. If problems persist, consult official support resources and include device model and firmware version in any support inquiry.
Security-minded operational tips
Use a hardware wallet for high-value holdings and keep only small amounts on hot wallets for daily use. Enable features such as transaction display confirmation and address verification on the hardware screen. Consider multi-signature arrangements for shared custody or institutional assets. Regularly review access logs and connected device lists within any custodial services you use, and maintain strict control over who has physical access to your devices.
Secure storage practices and routine checks
Adopt a clear routine for device custody and storage: mark a primary storage location that is physically secure, use tamper-evident bags when transporting devices, and document any custody handovers. Periodically perform a simulated recovery on a clean device to ensure your recovery seed works and you are familiar with the recovery steps — do this only in a safe, offline environment. Consider storing recovery information in multiple geographically separated, secure locations using secure methods such as bank safe deposit boxes or dedicated secure-storage services.
When to seek official support
Contact official Trezor support channels if you suspect device tampering, firmware downgrade attempts, or unexplained behavior. Provide only non-sensitive diagnostic information unless explicitly requested by verified support staff. Never share your PIN, passphrase, or recovery seed with anyone, including support representatives.